
September 10, 2025Use your fingerprints to unlock your phone, not a code or face.
January 8, 2026How do I Defend My Money as a Small Business.
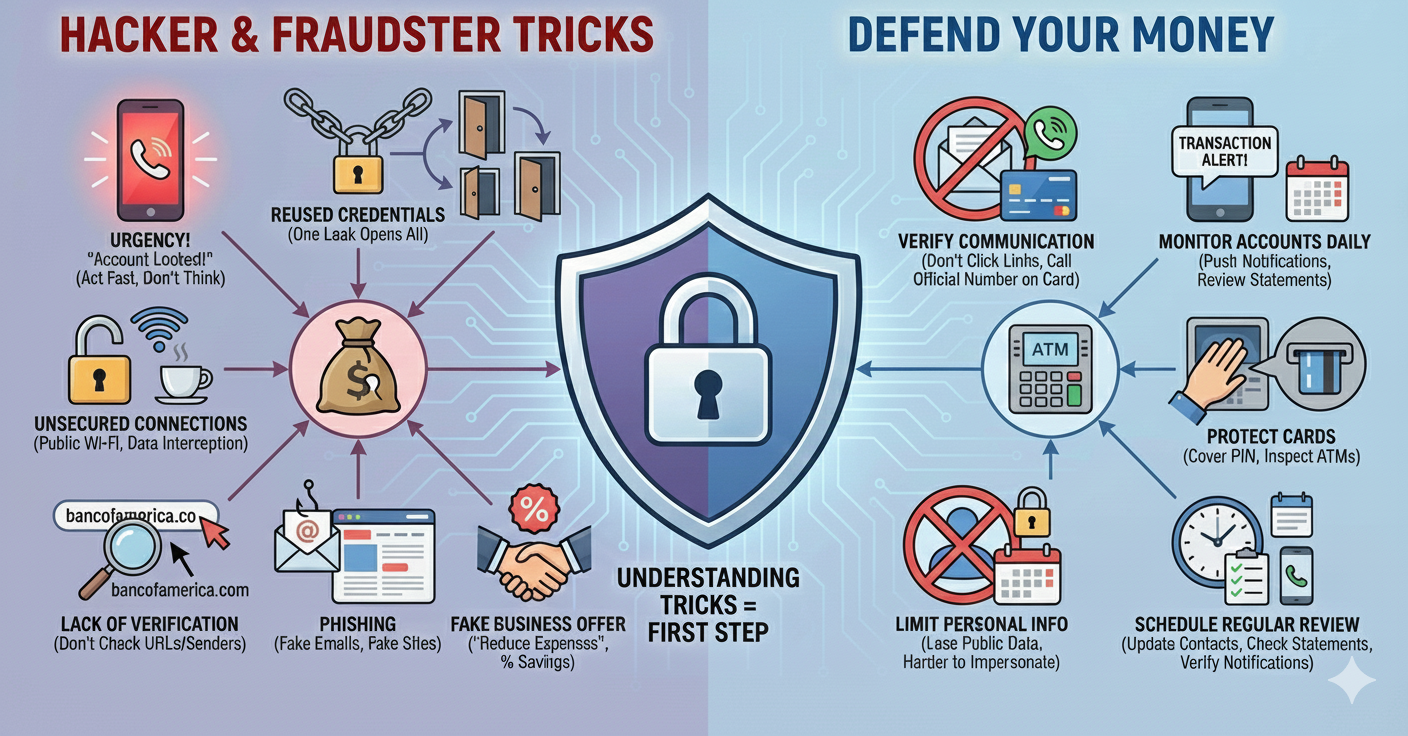
Understanding the common tricks is the first step to protecting your money.
Email especially can be a vulnerability. Verify Every Communication. Never click links in unexpected emails or texts.
When phoning your bank use the number on the back of your card, or programmed on your phone, or on your bank statement, not the one in an email message.
Monitor Accounts Daily (Set up push notifications for transactions from your bank.) Review statements for unknown charges.
Protect Credit Card and Debit Cards. Cover the keypad when entering your PIN. Inspect ATMs for tampering before use.
Limit Sharing Personal Info. The less data you post publicly (e.g., birthdate, travel plans), the harder it is for attackers to impersonate you or rob your home.
Schedule regular review and updates: Have your banking and other phone numbers available on your phone. Check your bank statements. Verify you are notified with large (or any) bank transactions. Verify you are notified about small balances!
Don't share your business expenses (like advertising costs, subscription costs, phone bills) with anyone.
For further details, subscribe to Cyber StepTracker where we provide full details including training, a checklist and guidance on avoiding these and many other cyber risks.
That is all.
Latest Articles

September 10, 2025Use your fingerprints to unlock your phone, not a code or face.
October 14, 2025Knowing how passwords are stored helps motivate you to make and keep good passwords.
September 24, 2025 updated January 14, 2026Six different ways to list the software apps installed on your computer.

November 19, 2025Well, could they? What are the protections on your ChatGPT sessions?

January 14, 2026Why is my telephone bill a secret? We explain the risks of people seeing your phone bill.

January 8, 2026How do I Defend My Money as a Small Business.

January 15, 2026We explain the difference between a Recovery Drive and a Windows Installation Drive.
February 2, 2026What are three different ways to backup my Windows computer?